Of their Carbis Bay verbal exchange, the G7 introduced their goal to paintings in combination to take on ransomware teams. Days later, US president Joe Biden met with Russian president Vladimir Putin, the place an extradition procedure to deliver Russian cybercriminals to justice in the USA used to be mentioned. Putin reportedly agreed in theory, however insisted that extradition be reciprocal. Time will inform if an extradition treaty may also be reached. However whether it is, who precisely will have to extradited – and what for?
You’ll pay attention to extra articles from The Dialog, narrated through Noa, right here.
The issue for legislation enforcement is that ransomware – a type of malware used to thieve organisations’ knowledge and cling it to ransom – is an excessively slippery fish. No longer simplest is it a combined crime, together with other offences throughout other our bodies of legislation, nevertheless it’s additionally against the law that straddles the remit of various policing businesses and, in lots of circumstances, international locations. And there’s no one key perpetrator. Ransomware assaults contain a allotted community of various cybercriminals, frequently unknown to one another to cut back the danger of arrest.
So it’s necessary to have a look at those assaults intimately to know the way the USA and the G7 may move about tackling the expanding selection of ransomware assaults we’ve observed all over the pandemic, with a minimum of 128 publicly disclosed incidents going down globally in Would possibly 2021.
What we discover after we attach the dots is a certified trade a ways got rid of from the organised crime playbook, which reputedly takes its inspiration directly from the pages of a industry research handbook.
The ransomware trade is answerable for an enormous quantity of disruption in nowadays’s international. No longer simplest do those assaults have a crippling financial impact, costing billions of bucks in harm, however the stolen knowledge got through attackers can proceed to cascade down during the crime chain and gas different cybercrimes.
Learn extra:
Ransomware gangs are working insurrection – paying them off does not assist
Ransomware assaults also are converting. The felony trade’s industry style has shifted in opposition to offering ransomware as a carrier. This implies operators give you the malicious device, arrange the extortion and fee techniques and arrange the popularity of the “emblem”. However to cut back their publicity to the danger of arrest, they recruit associates on beneficiant commissions to make use of their device to release assaults.
This has ended in an intensive distribution of felony labour, the place the individuals who personal the malware aren’t essentially the similar as those that plan or execute ransomware assaults. To complicate issues additional, each are assisted in committing their crimes through services and products introduced through the broader cybercrime ecosystem.

trambler58/Shutterstock
How do ransomware assaults paintings?
There are a number of levels to a ransomware assault, which I’ve teased out after analysing over 4,000 assaults from between 2012 and 2021.
First, there’s the reconnaissance, the place criminals determine doable sufferers and get right of entry to issues to their networks. That is adopted through a hacker gaining “preliminary get right of entry to”, the use of log-in credentials purchased at the darkish internet or bought via deception.
As soon as preliminary get right of entry to is received, attackers search to escalate their get right of entry to privileges, letting them seek for key organisational knowledge that may purpose the sufferer essentially the most ache when stolen and held to ransom. Because of this medical institution scientific data and police data are frequently the objective of ransomware assaults. This key knowledge is then extracted and stored through criminals – all ahead of any ransomware is put in and activated.
Subsequent comes the sufferer organisation’s first signal that they’ve been attacked: the ransomware is deployed, locking organisations from their key knowledge. The sufferer is instantly named and shamed by means of the ransomware gang’s leak website online, positioned at the darkish internet. That “press unlock” might also function threats to percentage stolen delicate knowledge, with the purpose of scary the sufferer into paying the ransom call for.
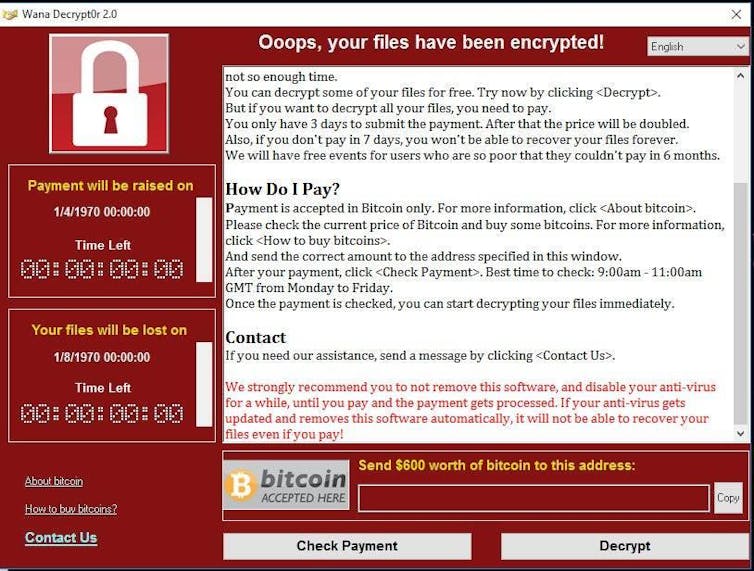
TechnoLlama, CC BY
A success ransomware assaults see the ransom paid in cryptocurrency, which is hard to track, and transformed and laundered into fiat forex. Cybercriminals frequently make investments the proceeds to give a boost to their functions – and to pay associates – so that they don’t get stuck.
The cybercrime ecosystem
Whilst it’s possible {that a} suitably professional perpetrator may just carry out each and every of the purposes, it’s extremely not likely. To cut back the danger of being stuck, perpetrator teams have a tendency to expand and grasp specialist abilities for various levels of an assault. Those teams get pleasure from this inter-dependency, because it offsets felony legal responsibility at each and every degree.
And there are many specialisations within the cybercrime underworld. There are spammers, who rent out spamware-as-a-service device that phishers, scammers, and fraudsters use to thieve folks’s credentials, and databrokers who business those stolen main points at the darkish internet.
They could be bought through “preliminary get right of entry to agents”, who specialize in gaining preliminary access to pc techniques ahead of promoting on the ones get right of entry to main points to would-be ransomware attackers. Those attackers frequently have interaction with crimeware-as-a-service agents, who rent out ransomware-as-a-service device in addition to different malicious malware.
To coordinate those teams, darkmarketeers supply on-line markets the place criminals can brazenly promote or business services and products, generally by means of the Tor community at the darkish internet. Monetisers are there to launder cryptocurrency and switch it into fiat forex, whilst negotiators, representing each sufferer and perpetrator, are employed to settle the ransom quantity.
This ecosystem is repeatedly evolving. For instance, a contemporary construction has been the emergence of the “ransomware guide”, who collects a rate for advising offenders at key levels of an assault.
Arresting offenders
Governments and legislation enforcement businesses seem to be ramping up their efforts to take on ransomware offenders, following a yr blighted through their persisted assaults. Because the G7 met in Cornwall in June 2021, Ukrainian and South Korean police forces coordinated to arrest components of the notorious CL0P ransomware gang. In the similar week, Russian nationwide Oleg Koshkin used to be convicted through a US court docket for working a malware encryption carrier that felony teams use to accomplish cyberattacks with out being detected through antivirus answers.
Whilst those traits are promising, ransomware assaults are a fancy crime involving a allotted community of offenders. Because the offenders have honed their strategies, legislation enforcers and cybersecurity professionals have attempted to stay tempo. However the relative inflexibility of policing preparations, and the loss of a key perpetrator (Mr or Mrs Large) to arrest, might at all times stay them one step in the back of the cybercriminals – even though an extradition treaty is struck between the USA and Russia.
Supply Through https://theconversation.com/inside-a-ransomware-attack-how-dark-webs-of-cybercriminals-collaborate-to-pull-them-off-163015




