Australian organisations are a comfortable goal for ransomware assaults, say mavens who the day before today issued a recent caution that the federal government must do extra to prevent companies and companies falling prey to cyber-crime. However in reality, the risk has been rising international for greater than 3 many years.
In spite of being a moderately new thought to the general public, ransomware has roots within the overdue Nineteen Eighties and has advanced considerably over the last decade, reaping billions of greenbacks in ill-gotten beneficial properties.
With names like Unhealthy Rabbit, Chimera and GoldenEye, ransomware has established a legendary high quality with an attract of poser and fascination. Except, in fact, you’re the goal.
Sufferers have few choices to be had to them; refusing to pay the ransom is determined by having excellent sufficient backup practices to recuperate the corrupted or stolen information.
In line with a learn about by way of safety corporate Coveware, 51% of companies surveyed had been hit with some form of ransomware in 2020. Extra concerningly nonetheless, standard ransom calls for are hiking dramatically, from a median of US$6,000 in 2018, to US$84,000 in 2019, and a staggering US$178,000 in 2020.
A short lived historical past of ransomware
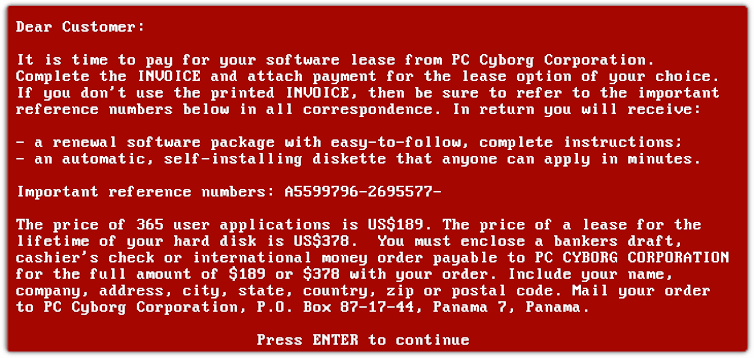
The primary identified instance of ransomware dates again to 1988-89. Joseph Popp, a biologist, dispensed floppy disks containing a survey (the “AIDS Knowledge Introductory Diskette”) to decide AIDS an infection dangers. Some 20,000 of them had been reportedly dispensed at a International Well being Group convention and by means of postal mailing lists. Unbeknown to these receiving the disks, it contained a virulent disease of its personal. The AIDS Trojan lay dormant on techniques earlier than locking customers’ information and critical a “licence price” to revive get admission to.
Joseph L. Popp, AIDS Knowledge Trojan creator, Public area, by means of Wikimedia Commons
Even if the malware was once inelegant and simply undone, it drew media consideration on the time as a brand new form of cyber risk. The call for for cost (by way of cheque to a PO field in Panama) was once primitive by way of comparability with fashionable approaches, which name for budget to be transferred electronically, continuously in cryptocurrencies.
It was once smartly over a decade earlier than ransomware really started to proliferate. Within the mid-2000s, more potent encryption allowed for simpler ransom campaigns with using uneven cryptography (during which two keys are used: one to encrypt, and a 2d, stored secret by way of the criminals, to decrypt), which intended even professional techniques directors may just not extract the keys from the malware.
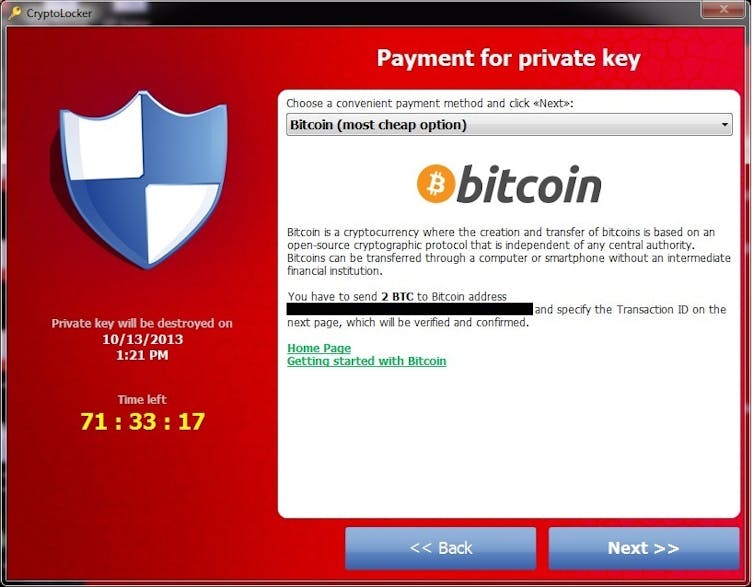
In 2013, CryptoLocker malware rose to international dominance, in part supported by way of the GameOver Zeus botnet. Cryptolocker encrypted customers’ information, sending the release key to a server managed by way of the criminals with a three-day closing date earlier than the important thing was once destroyed. The community was once close down in 2014, because of a significant international regulation enforcement effort known as Operation Tovar. It’s estimated to have impacted greater than 250,000 sufferers and doubtlessly garnered 42,000 Bitcoin, value round US$2 billion at as of late’s valuation.
Nikolai Grigorik, CC BY-SA 4.0 https://creativecommons.org/licenses/by-sa/4.0, by means of Wikimedia Commons
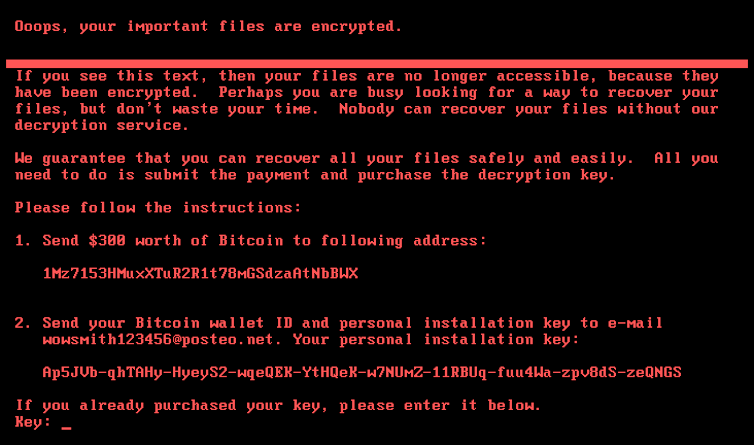
In 2016 there have been a number of high-profile incidents involving the Petya ransomware, which avoided customers from getting access to their onerous drives. It was once one of the most first vital examples of Ransomware as a Carrier, wherein legal gangs “promote” their ransomware equipment as a controlled provider.
Unknown legal. Notify the government, in case of discovery. Public area, by means of Wikimedia Commons
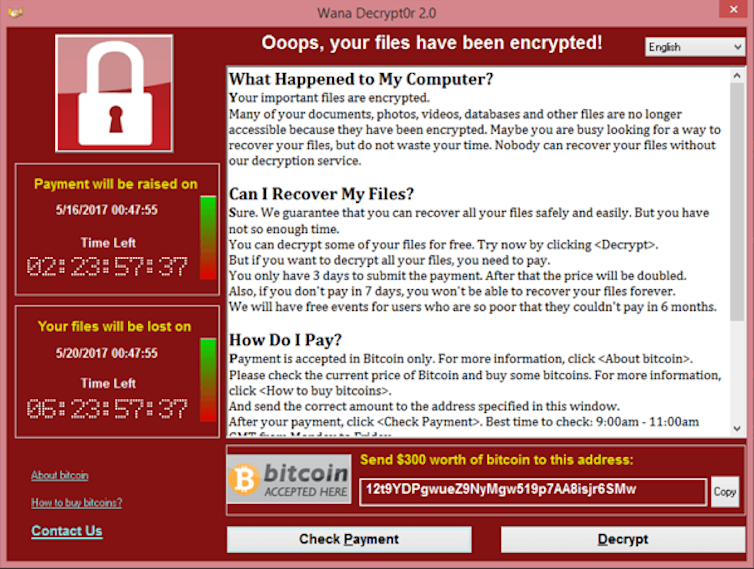
The next 12 months noticed arguably probably the most infamous ransomware assault of all time: the WannaCry assault. It struck loads of 1000’s of computer systems, together with an estimated 70,000 techniques on the UK Nationwide Well being Carrier. The worldwide have an effect on of WannaCry has been estimated at as much as US$4 billion.
Screenshot of a WannaCry ransomware assault on Home windows 8. Public area, by means of Wikimedia Commons
Newer nonetheless was once the Ryuk ransomware, which centered native councils and nationwide executive companies. However cyber-criminals have additionally attacked particular personal firms, together with the US’ greatest delicate oil distribution community, Colonial Pipeline, the multinational meat processor JBS Meals, and Australia’s Channel 9 community.
Is all ransomware the similar?
There are loads of varieties of ransomware, however they are compatible into a couple of large classes:
Crypto ransomware
In fashionable crypto ransomware assaults, the malware encrypts customers’ information (“locking” the information to lead them to unreadable) and can in most cases contain a “key” to release the information being saved on a faraway server managed by way of the cyber-criminals. Early variants will require the sufferer to shop for tool to release the information.
Locker ransomware
Locker ransomware is normally a extra advanced form of malware that goals a person’s complete working device (equivalent to Home windows, macOS or Android), hampering their talent to make use of their software. Examples can come with combating the pc from booting, or forcing a ransom call for window to seem within the foreground and combating interplay with the opposite programs.
Even if information don’t seem to be encrypted, the device is in most cases unusable by way of maximum customers (as you might most probably want any other device or tool to extract the information). In some instances the ransom calls for confer with executive companies with threats of investigations when it comes to tax fraud, ownership of kid abuse fabrics, or terrorist actions.

Motormille2, CC BY-SA 4.0 https://creativecommons.org/licenses/by-sa/4.0, by means of Wikimedia Commons
Leakware
In a leakware assault, the information don’t seem to be encrypted however as a substitute are stolen from the sufferer and held by way of cyber-criminals. It’s the specter of public unlock on my own this is used to safe a ransom cost. From 2020 to 2021, reported occurrences of non-encrypted ransoms have doubled.
Double extortion
Double extortion is an alarming building wherein no longer simplest is a cost required to safe unlock of encrypted organisation information, however there may be the added risk of public unlock.
Writer equipped
This method in most cases comes to information being stolen from the organisation right through the malware an infection procedure, then despatched to servers run by way of the cyber-criminals. To inspire cost, extracts is also posted on public-facing internet sites to turn out ownership of the information – coupled with threats to put up the rest information.
Ransomware as a Carrier (RaaS)
Early ransomware was once evolved by way of people however, as with any tool, ransomware has come of age. It’s now a multibillion-dollar business (an estimated US$20 billion in 2020) and is each bit as smartly designed and applied as any business tool.
Simply as Microsoft’s Place of job 365 has evolved right into a provider, the place as a substitute of shopping for the tool, you pay a per thirty days or annually subscription, so has ransomware. Ransomware as a Carrier (RaaS) lets in criminals to procure products and services, in most cases in go back for a lower of the ransom.
Learn extra:
Keeping the scoop to ransom? What we all know to this point concerning the Channel 9 cyber assault
To pay, or to not pay?
Maximum regulation enforcement companies counsel in opposition to ransom bills (simply as many governments won’t negotiate with terrorists), as a result of it’s prone to inspire long run assaults. However many organisations nonetheless do pay up. Curiously, the general public sector fingers over as much as ten occasions extra money to unlock their information than sufferers within the personal sector.
Paying a ransom is often observed because the lesser of 2 evils, specifically for smaller organisations that may in a different way be close down completely by way of the disruption to their techniques. Or, in case you are fortunate, the malware will have already got a publicly to be had antidote.
However paying the ransom doesn’t ensure you’ll get all of your information again. Through one estimate, a median of 65% of knowledge was once in most cases recovered after paying the ransom, and simplest 8% of organisations controlled to revive it all.
With legal teams now reaping multimillion-dollar income, ransomware assaults are prone to goal greater organisations the place the rewards are richer, in all probability that specialize in holders of precious highbrow belongings such because the health-care and clinical analysis sectors. The Web of Issues (IoT) can be a goal for cyber-criminals, with international networks of attached units held to ransom.
Whilst large organisations are prone to have suitable technical safeguards, person schooling remains to be key – a lapse of judgement from a unmarried particular person can nonetheless convey an organisation to its knees. For smaller firms, looking for (and following) cyber recommendation is a very powerful.
Given the massive scale on which cyber-criminals are actually working, we need to hope regulation enforcement and tool safety engineers can keep one step forward.
Learn extra:
Keeping the sector to ransom: the highest 5 most deadly legal organisations on-line at this time
Supply Through https://theconversation.com/is-australia-a-sitting-duck-for-ransomware-attacks-yes-and-the-danger-has-been-growing-for-30-years-161818




