“A 3rd of the Web is underneath assault. Thousands and thousands of community addresses had been subjected to dispensed denial-of-service (DDoS) assaults over two-year length,” reviews Warren Froelich at the UC San Diego Information Heart web page. A DDoS is a kind of denial-of-service (DoS) assault by which the attacker carries out an assault the usage of many resources dispensed during the community.
However is the journalist justified in his alarmist response? Sure and no. If one-third of the Web used to be underneath assault, then one in each 3 smartphones wouldn’t paintings, and one in each 3 computer systems can be offline. Once we go searching, we will see that that is clearly now not the case, and if we now depend so closely on our telephones and Wikipedia, this is because we have now come to view the Web as a community that purposes smartly.
Nonetheless, the DDoS phenomenon is actual. Contemporary assaults testify to this, such because the assault via the botnet Mirai at the French internet host OVH and the American internet host DynDNS. The internet sites owned via shoppers of those servers had been unavailable for a number of hours.
What the supply find out about truly checked out used to be the semblance of IP addresses within the strains of DDoS assaults. Over a length of 2 years, the authors discovered the addresses of 2 million other sufferers, out of the 6 million servers indexed on the internet.
Site visitors jams at the knowledge superhighway
Devices of information, referred to as packets, flow into at the Web community. When all of those packets wish to move to the similar position or take the similar trail, congestion happens, similar to the site visitors jams that happen on the finish of a workday.
It will have to be famous that generally it is vitally tricky, virtually unattainable, to distinguish between standard site visitors and denial of carrier assault site visitors. Site visitors generated via “flash crowd” and “slashdot impact” phenomena is similar to the site visitors witnessed all over this sort of assault.
Then again, this analogy simplest is going to this point, since packets are regularly arranged in flows, and the congestion at the community can result in those packets being destroyed, or the advent of recent packets, resulting in much more congestion. It’s subsequently a lot more difficult to treatment a denial-of-service assault on the internet than this can be a site visitors jam.
Everaldo Coelho and YellowIcon, CC BY
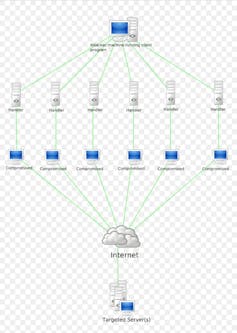
This sort of assault saturates the community hyperlink that connects the server to the Web. The attacker does this via sending numerous packets to the focused server. Those packets can also be despatched at once if the attacker controls numerous machines, a botnet.
Attackers additionally use the amplification mechanisms built-in in sure community protocols, such because the naming gadget (DNS) and clock synchronization (NTP). Those protocols are asymmetrical. The requests are small, however the responses can also be large.
In this sort of assault, an attacker contacts the DNS or NTP amplifiers via pretending to be a server that has been attacked. It then receives numerous unsolicited replies. Subsequently, even with a restricted connectivity, the attacker can create an important point of site visitors and saturate the community.
There also are “products and services” that provide the potential of purchasing denial of carrier assaults with various ranges of depth and periods, as proven in an investigation Brian Krebs performed after his personal website used to be attacked.
What are the effects?
For Web customers, the primary result is that the web page they wish to talk over with is unavailable.
For the sufferer of the assault, the primary result is a lack of source of revenue, which is able to take a number of bureaucracy. For a industrial web page, for instance, this loss is because of a loss of orders all over that length. For different web sites, it might outcome from dropping promoting earnings. This sort of assault permits an attacker to make use of advertisements rather than every other birthday party, enabling the attacker to faucet into the earnings generated via exhibiting them.
There were a couple of, uncommon institutional assaults. Probably the most documented instance is the assault towards Estonia in 2007, which used to be attributed to the Russian govt, even supposing this has been unattainable to turn out.
Direct monetary achieve for the attacker is unusual, alternatively, and is connected to the ransom calls for in change for finishing the assault.
Is it critical?
The affect an assault has on a carrier is determined by how widespread the carrier is. Customers subsequently revel in a low-level assault as a nuisance in the event that they wish to use the carrier in query.
Best sure large-scale occurrences, the newest being the Mirai botnet, have affects which can be perceived via a far greater target market.
Many servers and products and services are situated in non-public environments, and subsequently don’t seem to be available from the outdoor. Undertaking servers, for instance, are infrequently suffering from this type of assault. The important thing issue for vulnerability subsequently lies within the outsourcing of IT products and services, which is able to create a dependence at the community.
In spite of everything, an assault with an overly prime affect would, initially, be detected straight away (and subsequently regularly blocked inside a couple of hours), and in any case can be restricted via its personal actions (because the attacker’s conversation would additionally blocked), as proven via the outdated instance of the SQL Slammer computer virus.
In the end, the find out about displays that the phenomena of denial-of-service assaults via saturation were recurrent over the last two years. This information is important sufficient to reveal that this phenomenon should be addressed. But this isn’t a brand new incidence.
Different phenomena, reminiscent of routing manipulation, have the similar penalties for customers, like when Pakistan Telecom hijacked YouTube addresses.
Just right IT hygiene
Sadly, there’s no sure-fire type of coverage towards those assaults. After all, it comes all the way down to a topic of price of carrier and the volume of sources made to be had for reputable customers.
The “large” carrier suppliers have such a lot of sources that it’s tricky for an attacker to catch them off guard.
Nonetheless, this isn’t the tip of the Web, a long way from it. Then again, this phenomenon is one that are supposed to be restricted. For customers, just right IT hygiene practices will have to be adopted to restrict the hazards in their laptop being compromised, and therefore used to take part in this sort of assault.
It is usually necessary to check what form of coverage outsourced carrier providers have established, to make sure yes they have got enough capability and approach of coverage.
This text used to be translated from the unique French via the website I’MTech.
Supply By way of https://theconversation.com/when-the-internet-goes-down-92481




