Passwords had been used for 1000’s of years as a way of figuring out ourselves to others and in more moderen instances, to computer systems. It’s a easy thought – a shared piece of data, saved secret between people and used to “turn out” id.
Passwords in an IT context emerged within the Nineteen Sixties with mainframe computer systems – huge centrally operated computer systems with far off “terminals” for person get right of entry to. They’re now used for the entirety from the PIN we input at an ATM, to logging in to our computer systems and more than a few web pages.
However why can we want to “turn out” our id to the techniques we get right of entry to? And why are passwords so arduous to get proper?
Learn extra:
The lengthy historical past, and quick long term, of the password
What makes a just right password?
Till rather lately, a just right password would possibly had been a phrase or word of as low as six to 8 characters. However we’ve minimal period tips. That is on account of “entropy”.
When speaking about passwords, entropy is the measure of predictability. The mathematics in the back of this isn’t complicated, however let’s read about it with an excellent more effective measure: the choice of conceivable passwords, every now and then known as the “password area”.
If a one-character password best accommodates one lowercase letter, there are best 26 conceivable passwords (“a” to “z”). Via together with uppercase letters, we build up our password area to 52 doable passwords.
The password area continues to amplify because the period is larger and different personality varieties are added.
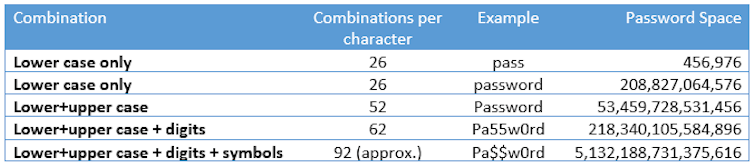
Taking a look on the above figures, it’s simple to know why we’re inspired to make use of lengthy passwords with higher and lowercase letters, numbers and logos. The extra complicated the password, the extra makes an attempt had to wager it.
Then again, the issue with relying on password complexity is that computer systems are extremely environment friendly at repeating duties – together with guessing passwords.
Final yr, a file used to be set for a pc looking to generate each and every imaginable password. It completed a charge quicker than 100,000,000,000 guesses according to moment.
Via leveraging this computing energy, cyber criminals can hack into techniques through bombarding them with as many password mixtures as conceivable, in a procedure referred to as brute drive assaults.
And with cloud-based era, guessing an eight-character password may also be completed in as low as 12 mins and value as low as US$25.
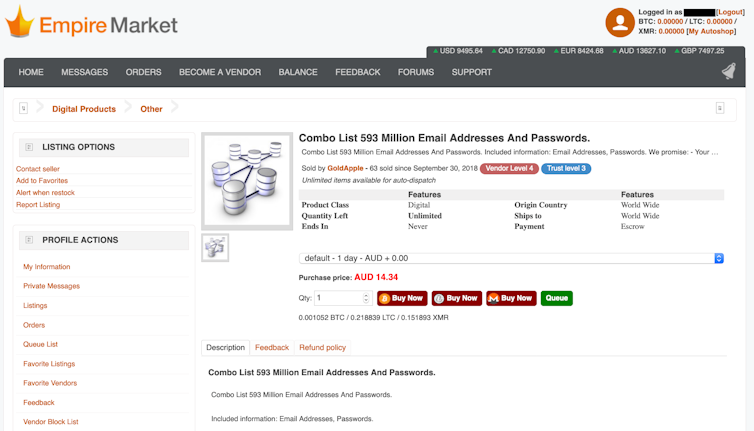
Additionally, as a result of passwords are virtually at all times used to offer get right of entry to to delicate knowledge or necessary techniques, this motivates cyber criminals to actively search them out. It additionally drives a profitable on-line marketplace promoting passwords, a few of which include electronic mail addresses and/or usernames.
How are passwords saved on web pages?
Web site passwords are most often saved in a secure method the usage of a mathematical set of rules referred to as hashing. A hashed password is unrecognisable and will’t be became again into the password (an irreversible procedure).
While you attempt to login, the password you input is hashed the usage of the similar procedure and in comparison to the model saved at the web site. This procedure is repeated every time you login.
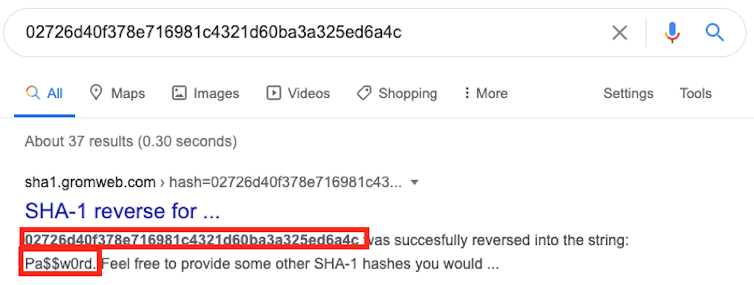
For instance, the password “Pa$$w0rd” is given the price “02726d40f378e716981c4321d60ba3a325ed6a4c” when calculated the usage of the SHA1 hashing set of rules. Check out it your self.
When confronted with a document stuffed with hashed passwords, a brute drive assault can be utilized, making an attempt each and every mixture of characters for a variety of password lengths. This has turn into such not unusual follow that there are web pages that checklist not unusual passwords along their (calculated) hashed price. You’ll merely seek for the hash to expose the corresponding password.
The robbery and promoting of passwords lists is now so not unusual, a devoted site — haveibeenpwned.com — is to be had to lend a hand customers test if their accounts are “within the wild”. This has grown to incorporate greater than 10 billion account main points.
In case your electronic mail cope with is indexed in this web site you will have to indisputably exchange the detected password, in addition to on every other websites for which you utilize the similar credentials.
Learn extra:
Will the hack of 500 million Yahoo accounts get everybody to offer protection to their passwords?
Is extra complexity the answer?
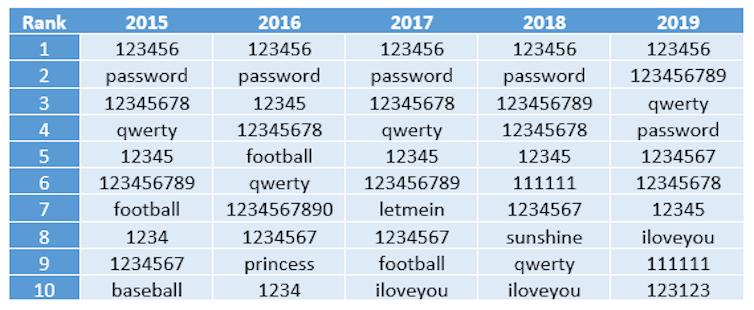
You possibly can assume with such a lot of password breaches going on day-to-day, we might have stepped forward our password variety practices. Sadly, final yr’s annual SplashData password survey has proven little exchange over 5 years.
As computing functions build up, the answer would seem to be larger complexity. However as people, we don’t seem to be professional at (nor motivated to) be mindful extremely complicated passwords.
We’ve additionally handed the purpose the place we use best two or 3 techniques desiring a password. It’s now not unusual to get right of entry to a lot of websites, with every requiring a password (regularly of various period and complexity). A up to date survey suggests there are, on reasonable, 70-80 passwords according to individual.
The excellent news is there are gear to handle those problems. Maximum computer systems now make stronger password garage in both the working machine or the internet browser, most often with the strategy to proportion saved knowledge throughout more than one units.
Examples come with Apple’s iCloud Keychain and the power to save lots of passwords in Web Explorer, Chrome and Firefox (even supposing much less dependable).
Password managers equivalent to KeePassXC can lend a hand customers generate lengthy, complicated passwords and retailer them in a safe location for once they’re wanted.
Whilst this location nonetheless must be secure (most often with a protracted “grasp password”), the usage of a password supervisor means that you can have a singular, complicated password for each and every site you consult with.
This gained’t save you a password from being stolen from a prone site. However whether it is stolen, you gained’t have to fret about converting the similar password on all of your different websites.
There are naturally vulnerabilities in those answers too, however possibly that’s a tale for some other day.
Learn extra:
Fb hack unearths the perils of the usage of a unmarried account to log in to different services and products
Supply Via https://theconversation.com/a-computer-can-guess-more-than-100-000-000-000-passwords-per-second-still-think-yours-is-secure-144418




